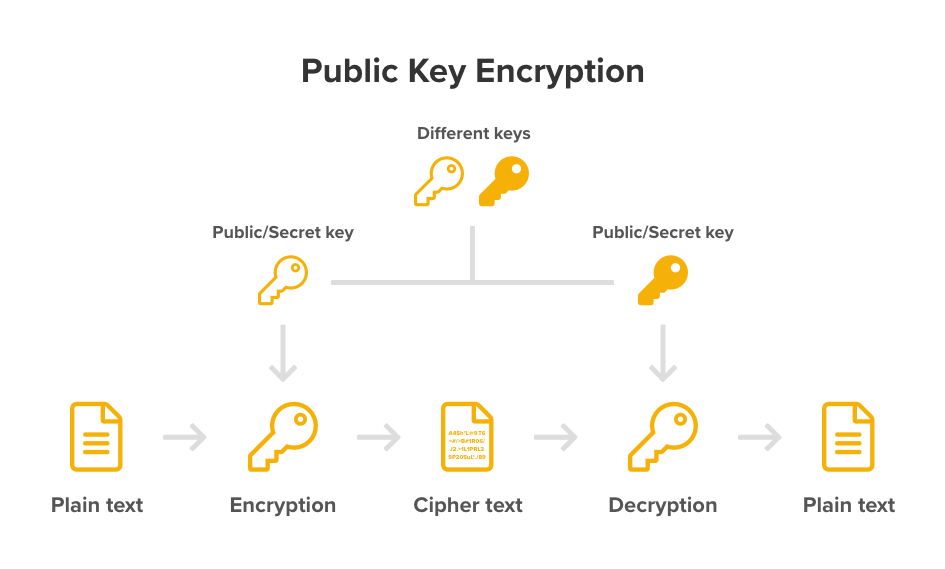
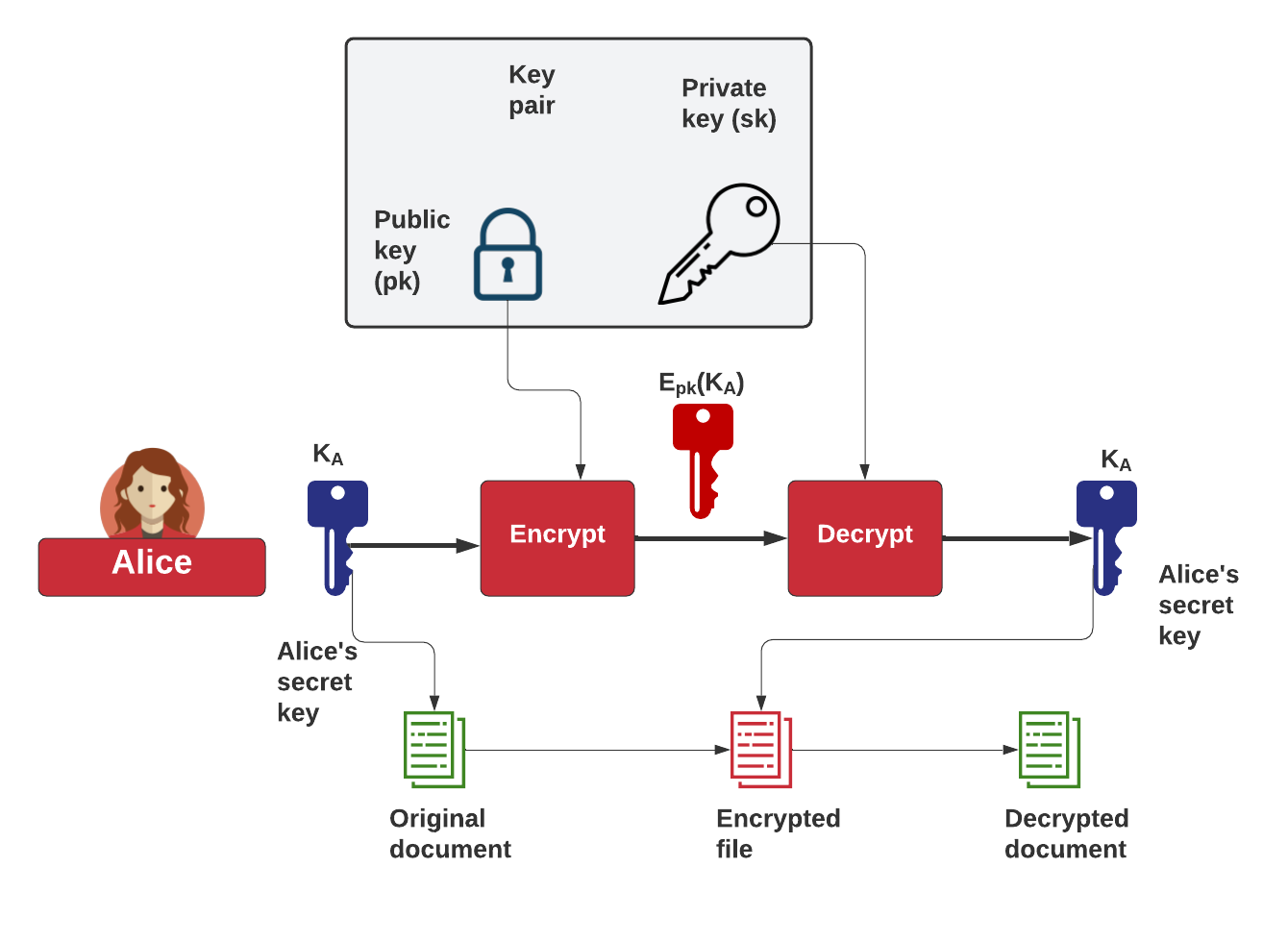
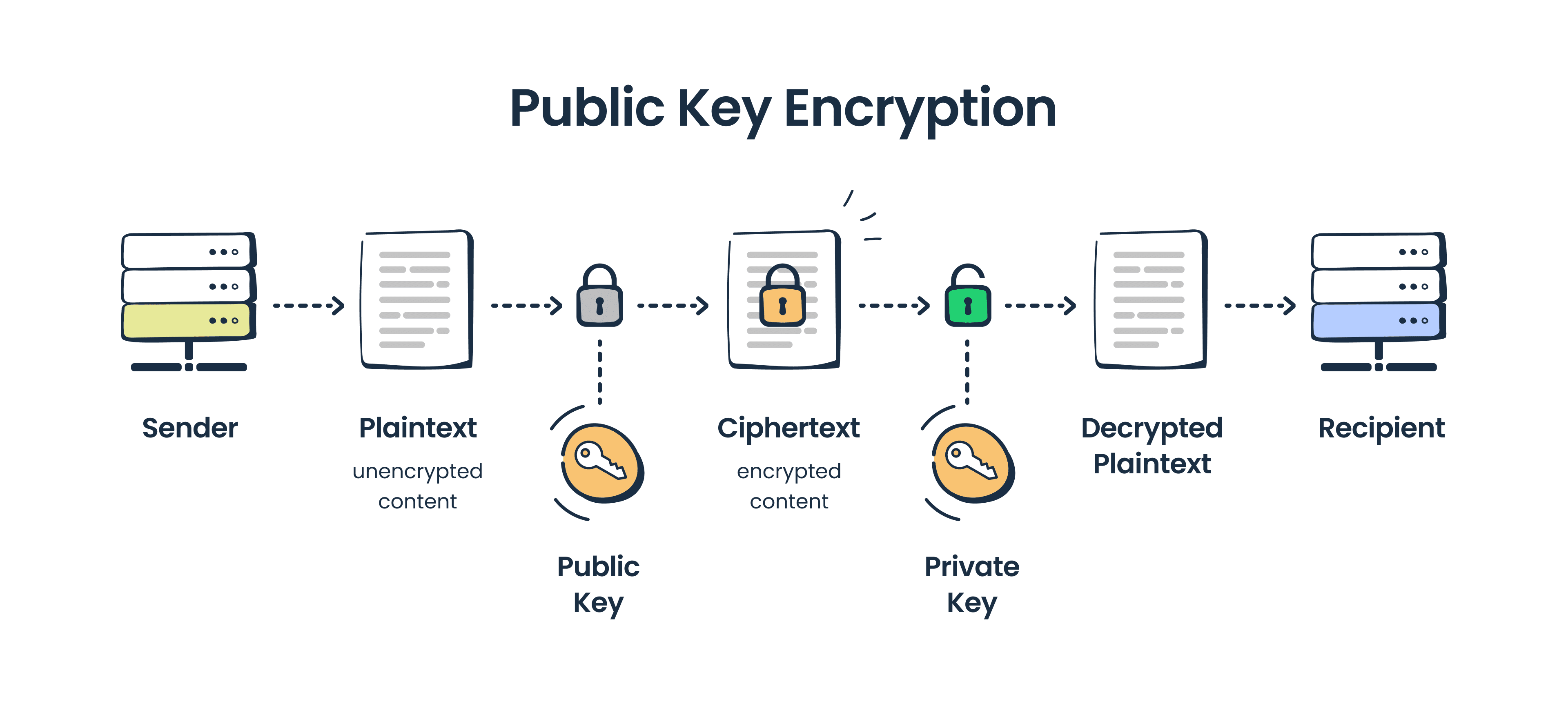
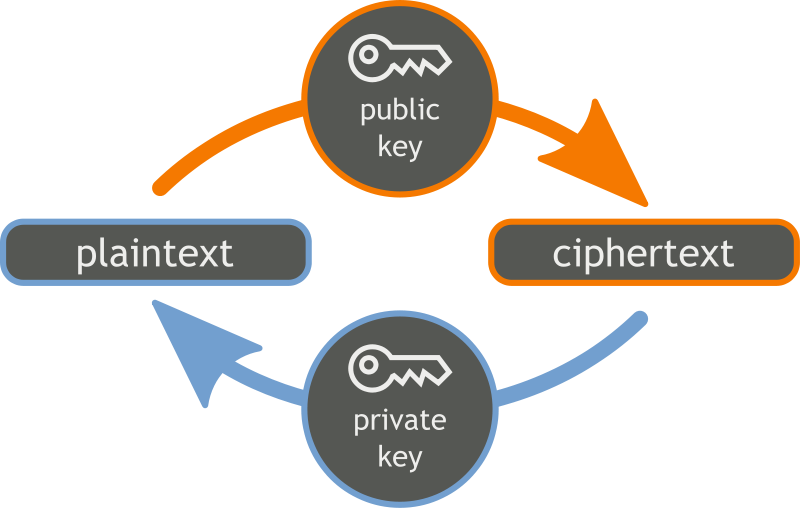
With public key cryptography, the private key is kept secure and private while the public key is publicly available. Here is an example of how the keys work to facilitate the exchange of confidential communications or a shared secret: If Alice and Bob want to exchange a secret message, Alice (the sender) will encrypt the message using Bob's.. So when a person uses asymmetric key encryption to send a message, both the sender and the recipient begin by generating a key pair (i.e. a public and a private key each) on their respective computers. A popular way of doing this is using the RSA algorithm, which comes up with a set of a public and private key that are mathematically linked to.
Cryptography 101 Sandfield
Public Key Cryptography

Public Key Encryption Definition & Example Lesson
Proxy Encryption Encrypting With Public Key, And Decrypt with Private Key

What Are Public Keys and Private Keys? Ledger
Email Encryption AllinOne Guide Mailtrap Blog

Public Keys vs Private Keys

Public Key vs Private Key How Do They Work? InfoSec Insights
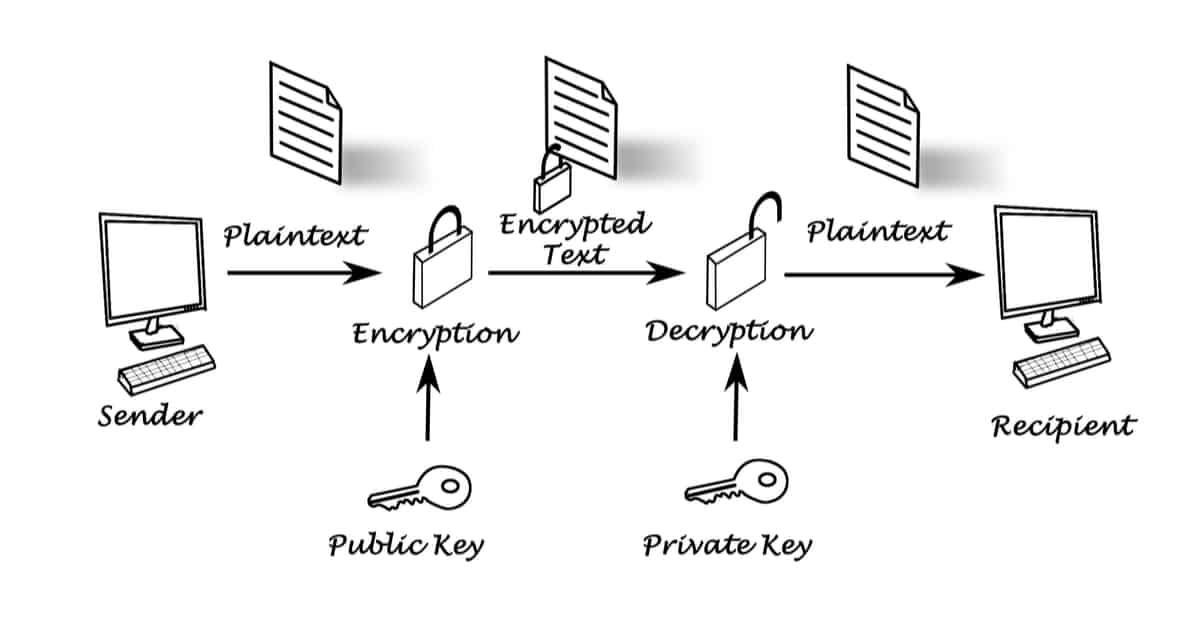
Public Key Cryptography The Complete Guide

What Is Public Key Cryptography? Explained Simply (Infographics!)
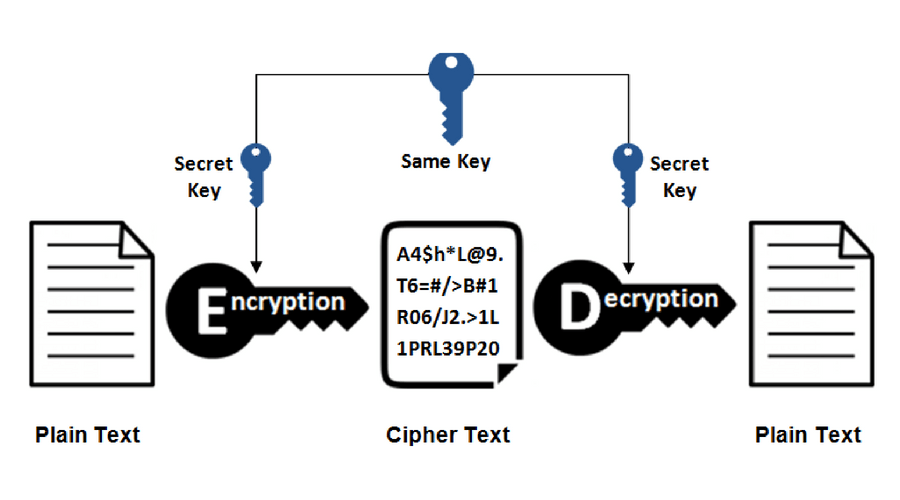
Cryptography Basics Ins and Outs of Encryption Springboard Blog
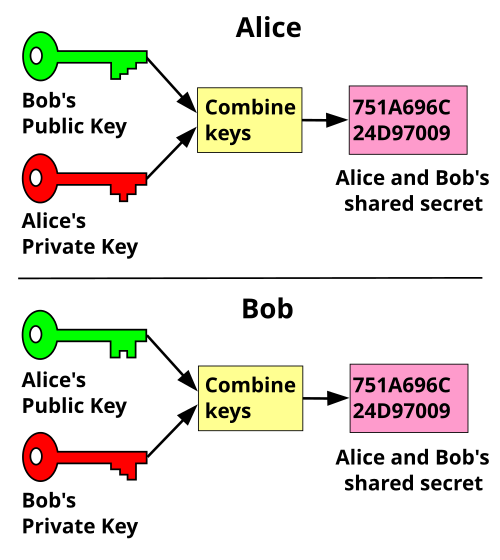
Publickey cryptography Wikipedia

Private Key Encryption Telegraph
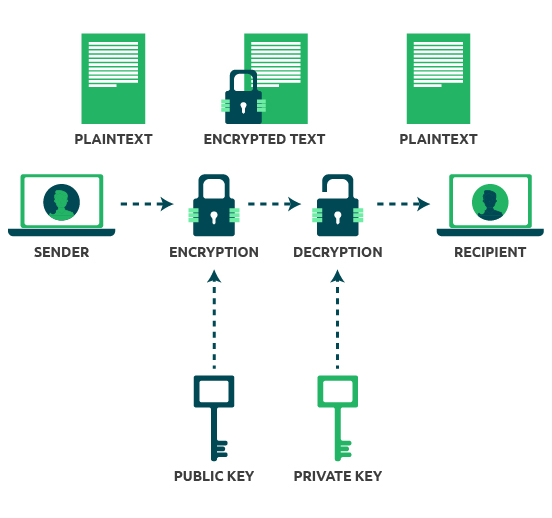
What is Public Key Encryption and How Does It Works?

How to Explain PublicKey Cryptography and Digital Signatures to NonTechies
Difference Between Public Key and Private Key in Cryptography

How Does Public Key Encryption Work?

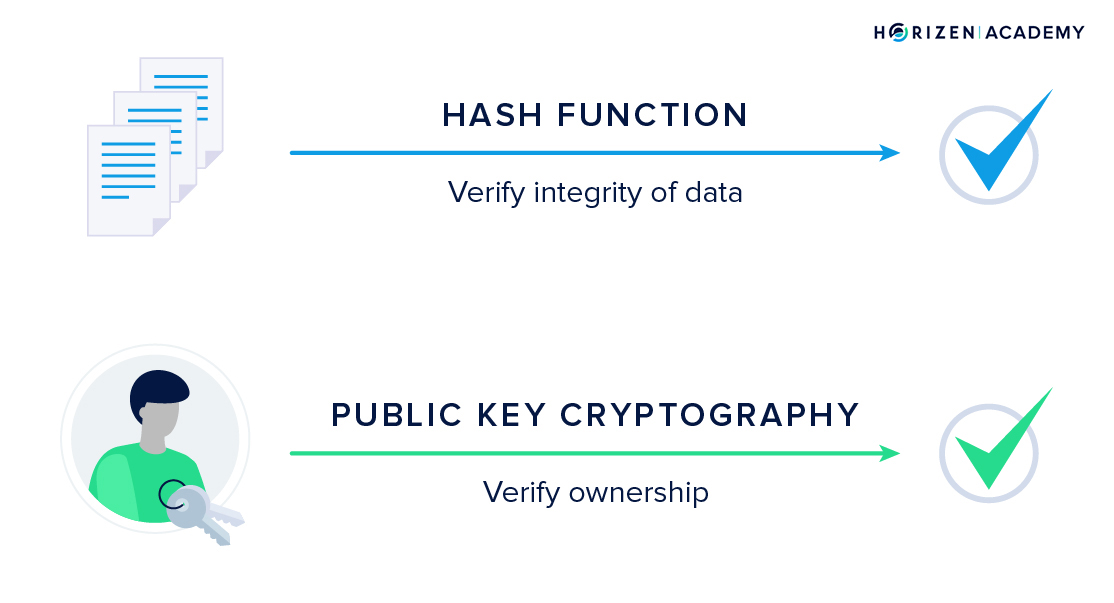
How Public Key Encryption Ensures Data Integrity

Public Key and Private Key Pairs How do they work?

What is Public Key Cryptography? Twilio
The sending computer encrypts the secret data using the receiving computer's public key and a mathematical operation. The power of public key encryption is in that mathematical operation. It's a "one-way function", which means it's incredibly difficult for a computer to reverse the operation and discover the original data.. Public key cryptography is a method of encrypting or signing data with two different keys and making one of the keys, the public key, available for anyone to use. The other key is known as the private key. Data encrypted with the public key can only be decrypted with the private key. Because of this use of two keys instead of one, public key.